Redirect URL using Istio/EnvoyFilter
We have a cool implementation, where istio takes care of the authentication flow. It checks if a header with a barrier token ( JWT token) or cookie with a token ( JWT token) is present from the application call. If it is not present it sends a 401 response. This is a good level of security for the services. However we have an application which does not understand security architecture, hence we have implemented a transparent redirect. This is common for most NGINX people. But to do it in Istio/Envoy it’s done like below:
# Source: istio-gateway/templates/envoy-filter.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: modify-401-to-302
spec:
workloadSelector:
labels:
app: istio-ingressgateway
configPatches:
- applyTo: HTTP_FILTER
match:
context: GATEWAY
listener:
filterChain:
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.lua
typed_config:
"@type": "type.googleapis.com/envoy.extensions.filters.http.lua.v3.Lua"
inline_code: |
function envoy_on_response(response_handle)
if response_handle:headers():get(":status") == "401" then
response_handle:logInfo("Got status 401, redirect to login...")
response_handle:headers():replace(":status", "302")
response_handle:headers():add("location", "https://abc.com")
end
end
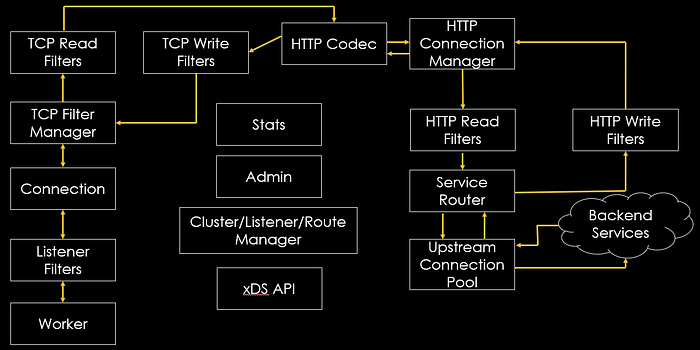
Understand Filter
workloadSelector:
In this example, the selector matches Envoy proxies that have a label “app” with value “istio-ingressgateway”.
By using the workload selector, you can selectively apply filters to specific Envoy proxies, which allows you to have fine-grained control over the processing of network traffic. This can be useful, for example, to apply different routing rules, security policies, or rate-limiting policies to different parts of your application.
applyTo:
The “applyTo” field is an array of strings, each of which specifies a different component that the filter should be applied to. Some of the possible values for the “applyTo” field include:
LISTENER: Applies the filter to all listeners in the data plane.NETWORK_FILTER: Applies the filter to all network filters in the data plane.ROUTE_CONFIGURATION: Applies the filter to all route configurations in the data plane.CLUSTER: Applies the filter to all clusters in the data plane.HTTP_FILTER: Applies the filter to all HTTP filters in the data plane.
context:
The specific config generation context to match on. Istio Pilot generates envoy configuration in the context of a gateway(GATEWAY), inbound traffic to sidecar (SIDECAR_INBOUND) and outbound traffic from sidecar(SIDECAR_OUTBOUND).
